Manufacturing leaders know that staying competitive means embracing digital transformation. Smart factories, connected production lines, and Industrial Internet of Things (IIoT) devices are no longer nice-to-haves: they're essential for operational efficiency and competitive advantage. But here's the uncomfortable truth: your traditional cybersecurity approach isn't keeping pace with these changes.
If you're still relying primarily on firewalls to protect your manufacturing operations, you're fighting tomorrow's battles with yesterday's weapons. The connected plant world demands a fundamentally different approach to cybersecurity, one that goes well beyond perimeter defenses.
Why Traditional Firewalls Fall Short in Smart Factories
Firewalls were designed for a different era: when IT systems were clearly separated from operational technology (OT), and when manufacturing equipment operated in isolation from corporate networks. That world no longer exists.
Today's smart factories blend IT and OT systems in ways that create entirely new attack vectors. When a programmable logic controller (PLC) communicates with an enterprise resource planning system, or when sensors on your production line send data to cloud analytics platforms, you've created pathways that traditional firewalls simply cannot adequately protect.
The fundamental issue is that firewalls are perimeter defenses. They're designed to keep threats out, but they're largely useless once an attacker has gained initial access to your network. In connected manufacturing environments, a single compromised device: whether it's a wireless printer, an environmental sensor, or even a security camera: can become the entry point for attackers to move laterally through your systems.
The Manufacturing Cybersecurity Crisis Nobody Talks About
Manufacturing now ranks as the third most targeted industry for cyberattacks, and the numbers are getting worse. Nearly half of manufacturing leaders identify cybersecurity as their greatest operational danger, yet most are operating with a false sense of security.
Here's the sobering reality: while 90% of manufacturers believe they have adequate cyberattack detection capabilities, very few have extended monitoring into their operational technology environments. The gap between perceived and actual cybersecurity readiness is enormous.
Manufacturing facilities now average 47 IoT devices per thousand square feet, and industry predictions suggest we'll see 125 billion connected IoT devices globally by 2030. Each of these devices represents a potential entry point for cybercriminals.
The Hidden Vulnerabilities of Connected Plants
The convergence of IT and OT systems creates vulnerabilities that many manufacturing leaders don't fully understand. Legacy operational technology systems: including SCADA systems, PLCs, and industrial control systems: were never designed with cybersecurity in mind. They were built for reliability and performance in isolated environments, not for security in connected networks.
When these systems connect to enterprise networks for efficiency gains, they bring their vulnerabilities with them. Many OT systems remain unpatched for months or even years because applying updates requires production downtime that manufacturers can't afford.
The problem compounds when you consider that newly acquired IIoT devices can be compromised during the manufacturing process itself, arriving at your facility with malicious code already embedded. When these devices go online, they can spread threats throughout your network before you even realize there's a problem.
Beyond Firewalls: What Modern Manufacturing Cybersecurity Looks Like
Effective cybersecurity in connected manufacturing environments requires a comprehensive approach that goes far beyond perimeter defenses. Here's what modern manufacturing cybersecurity actually involves:
Complete Asset Visibility and Inventory
You cannot protect what you cannot see. Conduct a comprehensive audit of all connected technology assets across both IT and OT environments. This includes everything from servers and workstations to sensors, controllers, and monitoring equipment. Classify each system by criticality and risk level.
Continuous Monitoring Across IT and OT Systems
Deploy monitoring solutions capable of detecting anomalous behavior throughout your connected systems, not just at network perimeters. This means extending security monitoring into operational environments and ensuring you can detect when normal equipment behavior patterns change.
Firmware and Device Validation
Implement processes to validate the integrity of new production equipment before deployment. This includes verifying that firmware hasn't been tampered with and that devices are free from embedded malware.
IT and OT Collaboration
Break down silos between IT security teams and operational personnel. Develop collaborative approaches that balance security requirements with operational needs. This often requires addressing authority conflicts around maintenance schedules, security software deployment, and system access controls.
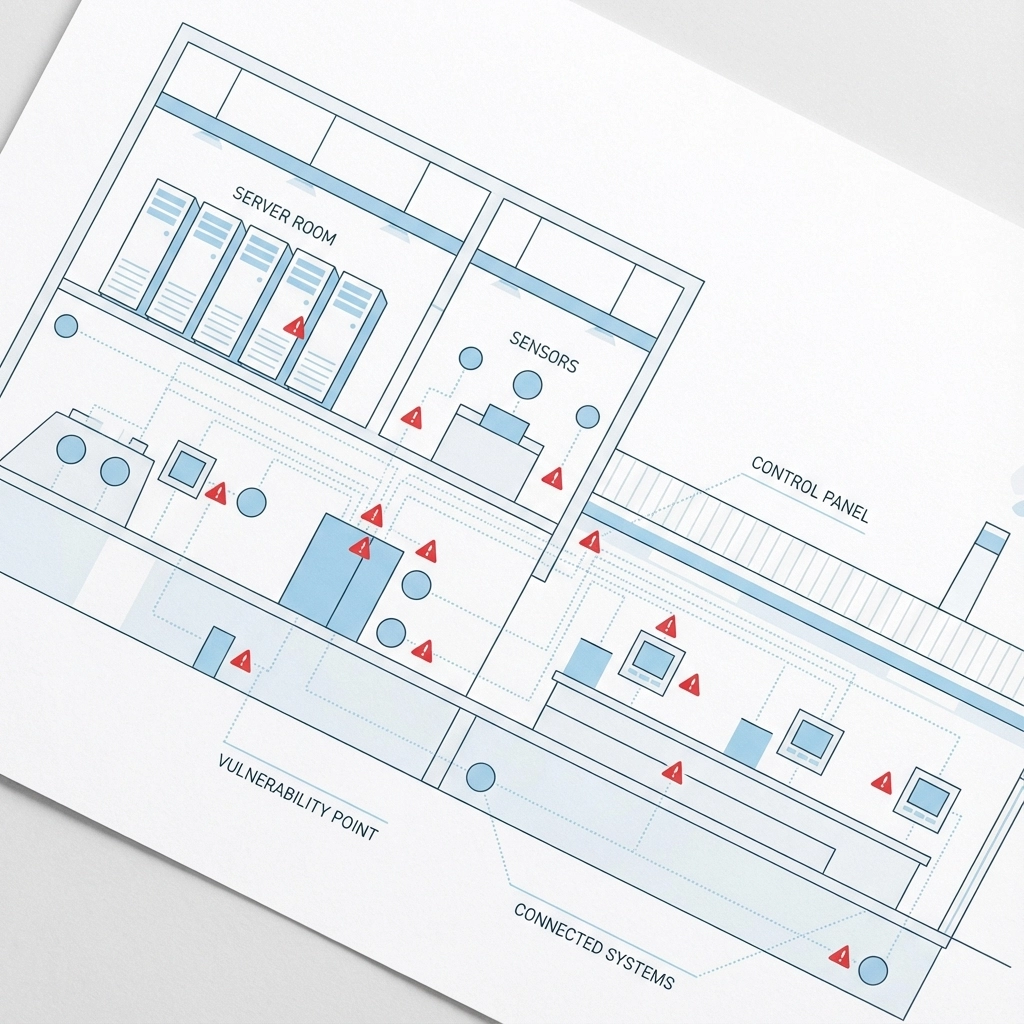
The Smart Factory Consulting Advantage
Smart factory consulting brings together cybersecurity expertise with deep understanding of manufacturing operations. This specialized approach recognizes that manufacturing cybersecurity isn't just about technology: it's about understanding how security measures impact production efficiency, maintenance schedules, and operational workflows.
Effective smart factory consulting addresses the unique challenges of manufacturing environments, including the need to maintain uptime while implementing security measures, the complexity of managing both legacy and modern systems, and the critical importance of protecting intellectual property and production processes.
Manufacturing Digital Transformation Done Right
Manufacturing digital transformation initiatives that don't prioritize cybersecurity from the outset often create more vulnerabilities than they solve. Successful digital transformation in manufacturing requires a security-first approach that considers cybersecurity implications at every stage of the journey.
This means evaluating the security implications of new technologies before implementation, designing network architectures that facilitate both connectivity and security, and ensuring that digital transformation initiatives enhance rather than compromise your security posture.
Building Resilience for the Connected Plant Future
The future of manufacturing is undeniably connected. The manufacturers who thrive will be those who embrace this connectivity while building robust cybersecurity capabilities that protect their operations, their people, and their competitive advantages.
This requires moving beyond the mindset that cybersecurity is an IT problem. In connected manufacturing environments, cybersecurity is an operational imperative that requires attention from leadership, investment in the right technologies and expertise, and a commitment to ongoing vigilance.
Take Action: Assess Your Current Cybersecurity Posture
Start by conducting an honest assessment of your current cybersecurity capabilities. How many connected devices are operating in your facility? Do you have visibility into all of them? Can you monitor for unusual behavior across both IT and OT systems? When was your last comprehensive security assessment?
If you're unsure about any of these questions, it's time to engage experts who understand both cybersecurity and manufacturing operations. The cost of proactive cybersecurity investment is always less than the cost of recovering from a successful cyberattack.
Your connected plant represents enormous opportunities for efficiency, quality improvement, and competitive advantage. Protecting those opportunities requires cybersecurity strategies designed for the connected manufacturing world: strategies that go well beyond traditional firewalls and perimeter defenses.
The question isn't whether you can afford to invest in comprehensive manufacturing cybersecurity. The question is whether you can afford not to.
